Load Balance Mikrotik BY Winbox
Preparation
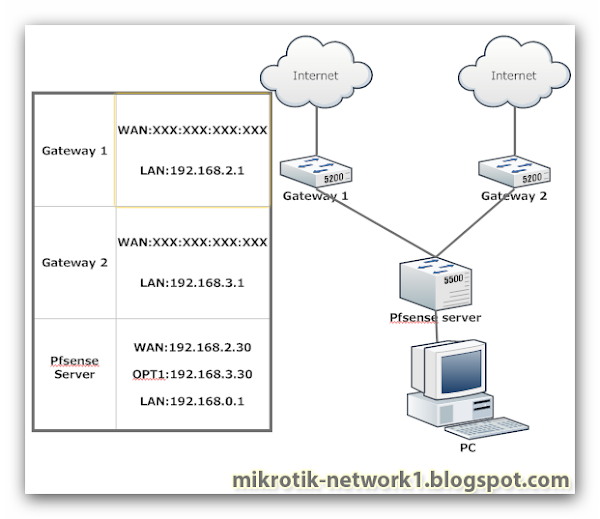
A. Configure existing modems with IP management as in the topology
• Modem green: 192.168.10.2 / 24
• Modem blue: 192.168.20.2 / 24
• Red Modem: 192.168.30.2 / 24
2. Configure PC workstation on the network with the IP as follows:
• IP: 192.168.1.x (x, from 2-254, because the one for the gateway)
• Netmask: 255.255.255.0
• Gateway: 192.168.1.1
Mikrotik Set Interface IP Address (IP> Address)
3. IP configuration by IP address mikrotik as follows:
Ether1: 192.168.1.1 / 24
Ether2: 192.168.10.1/24 (interface to the modem green)
Ether3: 192.168.20.1/24 (interface to the modem blue)
Ether4: 192.168.30.1/24 (red interface to the modem)
Note:
In this section we will name our connection. Conn_1 is the first connection, Conn_2, for the second connection, and Conn_3 for connection to 3.
Note:
Perform this connection marking 3 times, masing2 with NTH 31, 32 and 33, with the name Conn_1, Conn_2 and Conn_3
Route Mark
4. General
• Add chain: prerouting
• In Interface: Eth 1 (local network interface)
• Connection mark: conn_1
5. Action
• Action: routing mark
• New Connection mark: route_1
• Passtrough: no
Note:
In this section we will give our name on the routing. route_1 is the first route, route_2, for the second route, and route_3 for routing to 3.
Note:
Perform routing marking this 3 times, masing2 to Conn_1, Conn_2 and Conn_3, with the name route_1, route_2 and route_3
NAT (IP> Firewall> NAT)
NAT, Network Address Translation, is a process of addressing the changes. There are several types of NAT, which will be used in this process is the src-nat (source nat).
Src-nat is a change in the source of a packet.
A. General
• Chain: src nat
• In Interface: Eth 1 (local network interface)
• Connection mark: conn_1
2. Action
• Action : src nat
• To address : 192.168.10.1
Note:
Src-nat to do this 3 times with the rule as follows:
Conn_1 ==> 192.168.10.1
Conn_2 ==> 192.168.20.1
Conn_3 ==> 192.168.30.1
Policy Routing (IP> Route)
Routing policy is the routing arrangement. In this section we set up a gateway or an exit point for each group
A. General
• gateway: 192.168.10.2
• Routing mark: route_1
Note:
Src-nat to do this 4 times with the rule as follows:
route_1 ==> 192.168.10.2
route_2 ==> 192.168.20.2
route_3 ==> 192.168.30.2
default ==> 192.168.10.2
Preparation
A. Configure existing modems with IP management as in the topology
• Modem green: 192.168.10.2 / 24
• Modem blue: 192.168.20.2 / 24
• Red Modem: 192.168.30.2 / 24
2. Configure PC workstation on the network with the IP as follows:
• IP: 192.168.1.x (x, from 2-254, because the one for the gateway)
• Netmask: 255.255.255.0
• Gateway: 192.168.1.1
Mikrotik Set Interface IP Address (IP> Address)
3. IP configuration by IP address mikrotik as follows:
Ether1: 192.168.1.1 / 24
Ether2: 192.168.10.1/24 (interface to the modem green)
Ether3: 192.168.20.1/24 (interface to the modem blue)
Ether4: 192.168.30.1/24 (red interface to the modem)
Note:
After configuring the IP Address on mikrotik, recheck the connectivity between the modem with mikrotik.
ping 192.168.10.2
ping 192.168.20.2
ping 192.168.30.2
Mangling (IP> Firewall> Mangle)
Mangle a process of separation. On the mangle, in fact no change nothing on the package or we will send the data, but in this process only in the package checkbox.
Mark Connection
First we will do the connection mark.
A. General
• Add chain: prerouting
• In Interface: Eth 1 (local network interface)
• Connection State: new
2. Extra - nth
• Nth
a. Every: 3
b. Packet: 1
Note:
Nth part is determining whether the package will go into group 1, group 2 or group 3. For the third line, it will be made to the Nth rule 3 31, 32 and 33.
3. Action
• Action: mark the connection
• New Connection mark: conn_1
• Passtrough: yes
In this section we will name our connection. Conn_1 is the first connection, Conn_2, for the second connection, and Conn_3 for connection to 3.
Note:
Perform this connection marking 3 times, masing2 with NTH 31, 32 and 33, with the name Conn_1, Conn_2 and Conn_3
Route Mark
4. General
• Add chain: prerouting
• In Interface: Eth 1 (local network interface)
• Connection mark: conn_1
• Action: routing mark
• New Connection mark: route_1
• Passtrough: no
Note:
In this section we will give our name on the routing. route_1 is the first route, route_2, for the second route, and route_3 for routing to 3.
Note:
Perform routing marking this 3 times, masing2 to Conn_1, Conn_2 and Conn_3, with the name route_1, route_2 and route_3
NAT (IP> Firewall> NAT)
NAT, Network Address Translation, is a process of addressing the changes. There are several types of NAT, which will be used in this process is the src-nat (source nat).
Src-nat is a change in the source of a packet.
A. General
• Chain: src nat
• In Interface: Eth 1 (local network interface)
• Connection mark: conn_1
2. Action
• Action : src nat
• To address : 192.168.10.1
Note:
Src-nat to do this 3 times with the rule as follows:
Conn_1 ==> 192.168.10.1
Conn_2 ==> 192.168.20.1
Conn_3 ==> 192.168.30.1
Policy Routing (IP> Route)
Routing policy is the routing arrangement. In this section we set up a gateway or an exit point for each group
A. General
• gateway: 192.168.10.2
• Routing mark: route_1
Note:
Src-nat to do this 4 times with the rule as follows:
route_1 ==> 192.168.10.2
route_2 ==> 192.168.20.2
route_3 ==> 192.168.30.2
default ==> 192.168.10.2
See you in the next lesson
with you
Mohamed Samir
with you
Mohamed Samir