Hotspot Mikrotik 777
Technology has been used Bootstrap Compatible Mobile.
Design Hotspot-12 beautiful Server Mikrotik
Design Hot Spot Mikrotik Free
Hotspot login server free
Hotspot login server free.
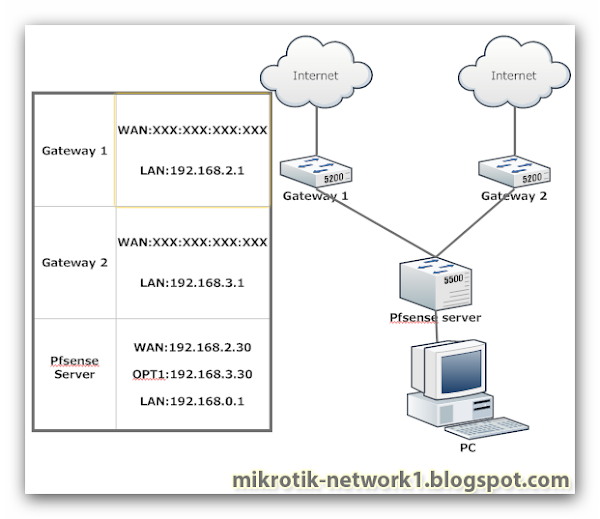
Merge 2 lines in server Pfsense?
Merge 2 lines in server Pfsense server free.
setup squid cahce in Ubuntu
How to setup squid cahce in Ubuntu ?
Tuesday, December 18, 2012
Monday, December 17, 2012
Hotspot Mikrotik Design
Hotspot Mikrotik Design
Design login page hotspot Mikrotik
Download click hear
Powered BY Mohamed samir
Thursday, November 29, 2012
Thursday, November 22, 2012
Tuesday, September 25, 2012
What’s New in Windows Server R2 ?
Quoting one of e-books
What’s New in Windows Server R2 ?
* What Is R2?
* The Focus for R2
* Top Reasons to Upgrade
******
What Is R2?
---------------------------------------------------------------*
Windows Server 2008 R2, or simply “R2” for short, is the second release of Windows
Server 2008. It isn’t a completely new release, but rather adds additional features and
refinements to the existing release.
Release Cadence
--------------------------------------------------------------*
Beginning with Windows Server 2003, Microsoft moved to a server release cycle that
was designed to have a major release every three to five years (Windows Server 2003,
Windows Server 2008), with a minor release at the approximate midpoint of the major
release cycle (Windows Server 2003 R2, Windows Server 2008 R2). This change allowed
Microsoft to move away from including new functionality in service packs (SPs), while
providing customers with a more stable and predictable server environment.
An R2 release is more than an SP, but less than a full major release. Windows Server
2008 R2 includes Windows Server 2008 SP2, but it also adds many new features and
functionality that were not part of Windows Server 2008.
Licensing and Packaging Changes
There are some minor licensing changes included in Windows Server 2008 R2, and one
completely new edition since the original release of Windows Server 2008. The new edition is
Windows Server 2008 R2 Foundation, an original equipment manufacturer (OEM)–only edition
that is an entry-level small-business solution limited to a maximum of 15 users, which has
several other restrictions as well.
More Info For more information on Windows Server 2008 R2 editions, includingWindowsServer 2008 R2 Foundation, and full details and edition comparisons for allWindowsServer 2008 R2 editions, see: http://www.microsoft.com/windowsserver2008/en/us/R2-editions.aspx.
The licensing of Windows Server 2008 R2 is very similar to that of Windows Server 2008,
and you can use Windows Server 2008 Client Access Licenses (CALs) for Windows Server 2008
R2 without having to upgrade your license. There is, however, one important difference that
is introduced with Windows Server 2008 R2—there is no requirement to upgrade to Windows
Server 2008 CALs when you install Windows Server 2008 R2 on a physical server that is only
used with the Hyper-V role.
Another difference between Windows Server 2008 and Windows Server 2008 R2 licensing
is caused by the name change from Terminal Services (TS) in Windows Server 2008 to Remote
Desktop Services (RDS) in Windows Server 2008 R2. This is more than just a name change,
and we cover the new features and functionality in depth in Chapter 4, “Remote Desktop Services
and VDI: Centralizing Desktop and Application Management.” However, for the licensing,
it really is just a name change—Windows Server 2008 R2 RDS CALs and Windows Server
2008 TS CALs can both be used for the full functionality of Windows Server 2008 R2 RDS.
There are also new license suite options in Windows Server 2008 R2, with the introduction
of the new Virtual Desktop Infrastructure (VDI) Standard and Virtual Desktop Infrastructure
Premium suites. We cover these new suite licenses in Chapter 4 when we talk about the new
VDI functionality that R2 makes possible.
The Focus for R2
--------------------------------------------------------------*
It would be presumptuous of us to talk about the “vision” that Microsoft had for Windows
Server 2008 R2, but we can certainly see a pattern in where the major improvements are:
Virtualization
Management
Scalability
Web
Networking and access
“Better Together” with Windows 7
We take a look at each of these areas throughout this book, but let’s start with a quick
high-level look at what has changed in each area.
Virtualization
Direct support for server virtualization, in the form of the Hyper-V hypervisor, was one of the
most important and highly anticipated improvements in Windows Server 2008. With the release
of Windows Server 2008 R2, Microsoft extends Hyper-V virtualization to include support
for client desktop virtualization, and adds important new capabilities for dynamic disk allocation,
live migration, and improved scalability and redundancy. We cover the improvements in
Hyper-V server virtualization capabilities in Chapter 3, “Hyper-V: Scaling and Migrating Virtual
Machines.”
Virtualization, however, isn’t limited to machine virtualization, but also includes presentation
virtualization (RDS), application virtualization (App-V), and client desktop virtualization
(VDI).
Windows Server 2008 R2 adds improvements in RDS that provide a more seamless integration
with Windows 7 clients, including full support for Windows Aero and multiple monitors.
Application virtualization support in R2 is improved, and the addition of the Remote Desktop
Virtualization Host (RD Virtualization Host) role service enables full desktop virtualization. We
cover VDI and RDS
Management
There are substantial improvements in the way Windows Server 2008 R2 can be managed,
both graphically and from the command line. A new version of Windows PowerShell
provides enhanced remote capabilities and is now available as an installation option for
Windows Server
Core. Graphical management is also improved, with Server Manager now
fully supported remotely, and many of the management consoles are better integrated into
Server Manager, enabling remote management. The improvements in Windows PowerShell
are covered
throughout the book, and we cover the specifics of setting up remote Server
Manager,
installing Windows PowerShell in Server Core, and many of the changes to rolebased
administration in Chapter 2, “Installation and Configuration: Adding R2 to Your World.”
Windows Server 2008 R2 includes a new Active Directory (AD) schema that enables an AD
Recycle Bin, a new set of Active Directory Windows PowerShell cmdlets, and improvements in
daily AD administration.
Improvements in storage management and file server management are part of Windows
Server 2008 R2. The new Windows File Classification Infrastructure (FCI) provides insight into
your data by automating classification processes so that you can manage your data more
effectively and economically. BranchCache improves bandwidth utilization of wide area
network
(WAN) connections by enabling local caching of data on Windows Server 2008 R2
and Windows 7 computers at branch offices. Improvements in processor utilization, startup
speed, and input/output (I/O) performance make the centralization of storage on iSCSI storage
area networks (SANs) easier and more efficient. We cover the details of file system and
storage.
Scalability
Windows Server 2008 R2 is the first version of Windows Server to support only 64-bit processors.
Further, Windows Server 2008 R2 now supports up to 256 logical processor cores for
a single operating system instance. Hyper-V virtual machines are able to address up to 64
logical cores in a single host. With the improvements in storage performance and efficiency,
and reduced graphical user interface (GUI) overhead, this gives Windows Server 2008 R2
the ability to scale up to larger workloads. Additionally, the R2 version of Hyper-V also adds
performance enhancements that increase virtual machine performance and reduce power
consumption. Hyper-V now supports Second Level Address Translation (SLAT), which uses
new features on today’s CPUs to improve virtual machine (VM) performance while reducing
processing load on the Windows Hypervisor. These improvements increase your ability to
consolidate workloads and servers onto fewer physical servers, reducing administration overhead,
power consumption, and rack costs. Chapters 2 and 3 cover these improvements.
Network Load Balancing (NLB) allows Windows Server 2008 R2 to scale out across multiple
servers. Windows Server 2008 R2 includes improvements in support for applications and
services that require persistent connections and also improves the health monitoring of NLB
clusters and the applications and services running on them.
Web
Windows Server 2008 R2 includes Internet Information Services (IIS) 7.5, an improved and
updated version of the IIS 7 that was included in Windows Server 2008. Windows Server 2008
R2 also includes a new Windows PowerShell provider for IIS to facilitate the automation of
management tasks. This Windows PowerShell provider is available on Server Core installations
of Windows Server 2008 R2 as well as full installations. IIS 7.5 also includes a new File Transfer
Protocol (FTP) server that supports Internet Protocol version 6 (IPv6), Secure Sockets Layer
(SSL), and Unicode characters.
Server Core can now include the Microsoft .NET Framework, giving administrators the
ability to manage IIS from Windows PowerShell or IIS Manager. As with many other areas of
R2, IIS 7.5 includes a Best Practices Analyzer (BPA) to simplify troubleshooting and configuration
of IIS. For full details on the new version of IIS, see Chapter 7, “IIS 7.5: Improving the Web
Application Platform.
Networking and Access
One of the most exciting new features in Windows Server 2008 R2 is DirectAccess, a new way
to securely connect remote clients to the corporate network. The most common method has
been virtual private networks (VPNs), which often require third-party client software running
on the client, and can be time-consuming to configure and troubleshoot. With Windows
Server 2008 R2 and DirectAccess, if the client is running Windows 7, the remote user has
seamless, always-on remote access to corporate resources that does not compromise the
secure aspects of remote connectivity.
DirectAccess works with the Network Access Protection (NAP) of Windows Server 2008 R2
to ensure that client computers meet your system health requirements, such as having security
updates and antimalware definitions installed, before allowing a DirectAccess connection.
Clients that are connected via DirectAccess can be remotely managed by internal IT staff,
allowing you to ensure that they are kept current with critical updates. DirectAccess is covered
in Chapter 8, “DirectAccess and Network Policy Server.”
Better Together with Windows 7
Many of the enhancements of Windows Server 2008 R2 are independent of the client operating
system being used, but others, such as DirectAccess, only work with Windows 7 clients.
Others, as is the case with the new RDS features, work better with a Windows 7 client, but are
still important improvements even if you’re running Windows Vista or Windows XP.
Some of the things that make Windows 7 and Windows Server 2008 R2 work better together
(and the technologies that enable them) are the following:
Simplified remote connectivity for remote users (DirectAccess)Secure remote connectivity, even from public computers (Remote Workplace plus RDGateway and RD Session Host) Improved branch office performance and security (BranchCache and read-only DistributedFile System Replication [DFS-R]) More efficient power management where the hardware supports it (Group Policy) Virtualized desktops (VDI) Improved removable drive security (BitLocker To Go)
Top Reasons to Upgrade
Windows Server 2008 R2 is not a free update to Windows Server 2008 unless you have Software
Assurance (SA). So should you upgrade? And why?
Well, the short answer is yes, you should upgrade. The why is what this book is all about in
many ways, but here are our top 10 reasons to upgrade:
Powerful hardware and scaling features
Windows Server 2008 R2 supports
up to 256 logical processors. R2 also supports SLAT, which enables R2 to take advantage
of the Enhanced Page Tables feature found in the latest AMD CPUs as well as the
similar Nested Page Tables feature found in Intel’s latest processors. The combination
enables R2 servers to run with much improved memory management.
Improved Hyper-V Hyper-V in Windows Server 2008 R2
can now access up to 64
logical CPUs on host computers—twice Hyper-V’s initial number of supported CPUs.
Live migration enables a highly fault-tolerant virtualization infrastructure, and dynamic
addition and removal of disks simplifies backup scenarios and overall management of
virtualized resources.
Reduced power consumption Windows Server 2008 R2
supports Core Parking,
which dynamically turns off unused processor cores when they aren’t needed, reducing
power consumption.
Reduced desktop costs Windows Server 2008 R2
enables VDI technology, which
extends the functionality of RDS to provide full desktop virtualization or application
virtualization of key applications.
Improved server management Windows Server 2008 R2
includes a new version
of Windows PowerShell, which is now available on Server Core as well. Server Manager
can now also be used remotely.
Improved branch office performance and security
Windows Server 2008 R2
includes BranchCache and read-only DFS-R, which extends the branch office scenarios
introduced in Windows Server 2008.
Improved Web server Windows Server 2008 R2
includes IIS 7.5 as well as a new
FTP server. IIS 7.5 includes a new Windows PowerShell provider for IIS management.
Windows PowerShell v2 Windows Server 2008 R2
includes an improved and
more powerful version of Windows PowerShell that has cmdlet support for remote
management. Windows PowerShell is now available on Server Core in Windows Server
2008 R2.
Improved Remote Desktop Services
The new RDS features provide an improved
and more seamless user experience, especially when the client is running Windows 7.
Improved mobile user experience
Mobile users running Windows 7 have seamless
and continuous access to corporate resources through DirectAccess. And RD Web
Access, shown in Figure 1-1, provides users running at least Windows XP SP3 with full
access to published applications or desktops.
Tuesday, August 28, 2012
Chat Applications for Ubuntu
Quoting one of e-books
Chat Applications for Ubuntu
1. Overview:
In this section, we will discuss how to install and configure a IRC server, ircd-irc2. We will also discuss how to install and configure Jabber, an instance messaging server.
2. IRC Server:
The Ubuntu repository has many Internet Relay Chat servers. This section explains how to install and
configure the original IRC server ircd-irc2.
2.1. Installation:
To install ircd-irc2, run the following command in the command prompt:
sudo apt-get install ircd-irc2
The configuration files are stored in /etc/ircd directory. The documents are available in /usr/
share/doc/ircd-irc2 directory.
2.2. Configuration:
The IRC settings can be done in the configuration file /etc/ircd/ircd.conf. You can set the IRC
host name in this file by editing the following line:
M:irc.localhost::Debian ircd default configuration::000APlease make sure you add DNS aliases for the IRC host name. For instance, if you set
irc.livecipher.com as IRC host name, please make sure irc.livecipher.com is resolvable in your
Domain Name Server. The IRC host name should not be same as the host name.
The IRC admin details can be configured by editing the following line:
A:Organization, IRC dept.:Daemon <ircd@example.irc.org>:Client Server::IRCnet:
You should add specific lines to configure the list of IRC ports to listen on, to configure Operator credentials, to configure client authentication, etc. For details, please refer to the example
configuration file
/usr/share/doc/ircd-irc2/ircd.conf.example.gz.
The IRC banner to be displayed in the IRC client, when the user connects to the server can be set in /etc/ircd/ircd.motd file.
After making necessary changes to the configuration file, you can restart the IRC server using
following command:
sudo /etc/init.d/ircd-irc2 restart
2.3. References:
You may also be interested to take a look at other IRC servers available in Ubuntu Repository. It
includes, ircd-ircu and ircd-hybrid.
• Refer to IRCD FAQ1 for more details about the IRC Server.
3. Jabber Instant Messaging Server
Jabber a popular instant message protocol is based on XMPP, an open standard for instant messaging, and used by many popular applications. This section covers setting up a Jabberd 2 server on a local LAN. This configuration can also be adapted to providing messaging services to users over the Internet.
3.1. Installation:
To install jabberd2, in a terminal enter:
sudo apt-get install jabberd2
3.2. Configuration :
A couple of XML configuration files will be used to configure jabberd2 for Berkeley DB user authentication. This is a very simple form of authentication. However, jabberd2 can be configured to
use LDAP, MySQL, PostgreSQL, etc for for user authentication.
First, edit /etc/jabberd2/sm.xml changing:
<id>jabber.example.com</id>
Note:
Replace jabber.example.com with the hostname, or other id, of your server.
Now in the <storage> section change the <driver> to:
<driver>db</driver>Next, edit /etc/jabberd2/c2s.xml in the <local> section change:
<id>jabber.example.com</id>
And in the <authreg> section adjust the <module> section to:
<module>db</module>
Finally, restart jabberd2 to enable the new settings:
sudo /etc/init.d/jabberd2 restart
You should now be able to connect to the server using a Jabber client like Pidgin for example.
Note:
The advantage of using Berkeley DB for user data is that after being configured no additional maintenance is required. If you need more control over user accounts and credentials another authentication method is recommended.
3.3. References:
• The Jabberd2 Web Site2 contains more details on configuring Jabberd2.
• For more authentication options see the Jabberd2 Install Guide3.
• Also, the Setting Up Jabber Server Ubuntu Wiki4 page has more information.
See you in the next lesson
Mr.Mohamed samir™
Monday, August 27, 2012
Mail Filtering for Ubuntu
Quoting one of e-books
Mail Filtering:
One of the largest issues with email today is the problem of Unsolicited Bulk Email (UBE). Also known as SPAM, such messages may also carry viruses and other forms of malware. According to some reports these messages make up the bulk of all email traffic on the Internet.
This section will cover integrating Amavisd-new, Spamassassin, and ClamAV with the Postfix Mail Transport Agent (MTA). Postfix can also check email validity by passing it through external content
filters. These filters can sometimes determine if a message is spam without needing to process it with more resource intensive applications. Two common filters are opendkim and python-policyd-spf.
• Amavisd-new is a wrapper program that can call any number of content filtering programs for spam
detection, antivirus, etc.
• Spamassassin uses a variety of mechanisms to filter email based on the message content.
• ClamAV is an open source antivirus application.
• opendkim implements a Sendmail Mail Filter (Milter) for the DomainKeys Identified Mail (DKIM)
standard.
• python-policyd-spf enables Sender Policy Framework (SPF) checking with Postfix.
This is how the pieces fit together:
• An email message is accepted by Postfix.
• The message is passed through any external filters opendkim and python-policyd-spf in this case.
• Amavisd-new then processes the message.
• ClamAV is used to scan the message. If the message contains a virus Postfix will reject the
message.
• Clean messages will then be analyzed by Spamassassin to find out if the message is spam.
Spamassassin will then add X-Header lines allowing Amavisd-new to further manipulate the message.
For example, if a message has a Spam score of over fifty the message could be automatically dropped from the queue without the recipient ever having to be bothered. Another, way to handle flagged messages is to deliver them to the Mail User Agent (MUA) allowing the user to deal with the message as they see fit.
Installation:
To install the rest of the applications enter the following from a terminal prompt:
sudo apt-get install amavisd-new spamassassin clamav-daemon
sudo apt-get install opendkim postfix-policyd-spf-python
There are some optional packages that integrate with Spamassassin for better spam detection:
sudo apt-get install pyzor razor
Along with the main filtering applications compression utilities are needed to process some email attachments:
sudo apt-get install arj cabextract cpio lha nomarch pax rar unrar unzip zip
Note:
If some packages are not found, check that the multiverse repository is enabled in /etc/apt/
sources.list
If you make changes to the file, be sure to run sudo apt-get update before trying to install again.
Configuration:
Now configure everything to work together and filter email.
ClamAV:
The default behaviour of ClamAV will fit our needs. For more ClamAV configuration options, check the configuration files in /etc/clamav.
Add the clamav user to the amavis group in order for Amavisd-new to have the appropriate access to scan files:
sudo adduser clamav amavis
sudo adduser amavis clamav
Spamassassin:
Spamassassin automatically detects optional components and will use them if they are present. This means that there is no need to configure pyzor and razor.
Edit /etc/default/spamassassin to activate the Spamassassin daemon. Change ENABLED=0 to:
ENABLED=1
Now start the daemon:
sudo /etc/init.d/spamassassin start
Amavisd-new:
First activate spam and antivirus detection in Amavisd-new by editing
/etc/amavis/conf.d/15-content_filter_mode:
use strict;
# You can modify this file to re-enable SPAM checking through spamassassin
# and to re-enable antivirus checking.
#
# Default antivirus checking mode
# Uncomment the two lines below to enable it
#
@bypass_virus_checks_maps = (
\%bypass_virus_checks, \@bypass_virus_checks_acl, \$bypass_virus_checks_re);
#
# Default SPAM checking mode
# Uncomment the two lines below to enable it
#
@bypass_spam_checks_maps = (
\%bypass_spam_checks, \@bypass_spam_checks_acl, \$bypass_spam_checks_re);
1; # insure a defined return
Bouncing spam can be a bad idea as the return address is often faked. Consider editing /etc/amavis/ conf.d/20-debian_defaults to set $final_spam_destiny to D_DISCARD rather than D_BOUNCE,
as follows:
$final_spam_destiny = D_DISCARD;
Additionally, you may want to adjust the following options to flag more messages as spam:
$sa_tag_level_deflt = -999; # add spam info headers if at, or above that level
$sa_tag2_level_deflt = 6.0; # add 'spam detected' headers at that level
$sa_kill_level_deflt = 21.0; # triggers spam evasive actions
$sa_dsn_cutoff_level = 4; # spam level beyond which a DSN is not sent
If the server's hostname is different from the domain's MX record you may need to manually set the $myhostname option. Also, if the server receives mail for multiple domains the @local_domains_acl
option will need to be customized. Edit the /etc/amavis/conf.d/50-user file:
$myhostname = 'mail.example.com';
@local_domains_acl = ( "example.com", "example.org" );
If you want to cover multiple domains you can use the following in the/etc/amavis/conf.d/50-user
@local_domains_acl = qw(.);
After configuration Amavisd-new needs to be restarted:
sudo /etc/init.d/amavis restart
DKIM Whitelist:
Amavisd-new can be configured to automatically Whitelist addresses from domains with
valid Domain Keys. There are some pre-configured domains in the /etc/amavis/conf.d/40-
policy_banks.
There are multiple ways to configure the Whitelist for a domain:
• 'example.com' => 'WHITELIST',: will whitelist any address from the "example.com" domain.
• '.example.com' => 'WHITELIST',: will whitelist any address from any subdomains of
"example.com" that have a valid signature.
• '.example.com/@example.com' => 'WHITELIST',: will whitelist subdomains of "example.com" that
use the signature of example.com the parent domain.
• './@example.com' => 'WHITELIST',: adds addresses that have a valid signature from
"example.com". This is usually used for discussion groups that sign their messages.
A domain can also have multiple Whitelist configurations. After editing the file, restart amavisd-new:
sudo /etc/init.d/amavis restart
Note:
In this context, once a domain has been added to the Whitelist the message will not receive
any anti-virus or spam filtering. This may or may not be the intended behavior you wish for
a domain.
Postfix
For Postfix integration, enter the following from a terminal prompt:
sudo postconf -e 'content_filter = smtp-amavis:[127.0.0.1]:10024'
Next edit /etc/postfix/master.cf and add the following to the end of the file:
smtp - amavis unix - - - - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
-o disable_dns_lookups=yes
-o max_use=20
127.0.0.1:10025 inet n - - - - smtpd
-o content_filter=
-o local_recipient_maps=
-o relay_recipient_maps=
-o smtpd_restriction_classes=
-o smtpd_delay_reject=no
-o smtpd_client_restrictions=permit_mynetworks,reject
-o smtpd_helo_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o smtpd_data_restrictions=reject_unauth_pipelining
-o smtpd_end_of_data_restrictions=
-o mynetworks=127.0.0.0/8
-o smtpd_error_sleep_time=0
-o smtpd_soft_error_limit=1001
-o smtpd_hard_error_limit=1000
-o smtpd_client_connection_count_limit=0
-o smtpd_client_connection_rate_limit=0
-o receive_override_options=no_header_body_checks,no_unknown_recipient_checks
Also add the following two lines immediately below the "pickup" transport service:
-o content_filter=
-o receive_override_options=no_header_body_checks
This will prevent messages that are generated to report on spam from being classified as spam.
Now restart Postfix:
sudo /etc/init.d/postfix restart
Content filtering with spam and virus detection is now enabled.
Amavisd-new and Spamassassin:
When integrating Amavisd-new with Spamassassin, if you choose to disable the bayes filtering by editing /etc/spamassassin/local.cf and use cron to update the nightly rules, the result can cause a
situation where a large amount of error messages are sent to the amavis user via the amavisd-new cron
job.
There are several ways to handle this situation:
• Configure your MDA to filter messages you do not wish to see.
• Change /usr/sbin/amavisd-new-cronjob to check for use_bayes 0. For example, edit /usr/sbin/ amavisd-new-cronjob and add the following to the top before the test statements:
egrep -q "^[ \t]*use_bayes[ \t]*0" /etc/spamassassin/local.cf && exit 0
Testing:
First, test that the Amavisd-new SMTP is listening:
telnet localhost 10024
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
220 [127.0.0.1] ESMTP amavisd-new service ready
^]
In the Header of messages that go through the content filter you should see:
X-Spam-Level:
X-Virus-Scanned: Debian amavisd-new at example.com
X-Spam-Status: No, hits=-2.3 tagged_above=-1000.0 required=5.0 tests=AWL, BAYES_00
X-Spam-Level:
Note:
Your output will vary, but the important thing is that there are X-Virus-Scanned and XSpam-Status entries.
Troubleshooting:
The best way to figure out why something is going wrong is to check the log files.
• For instructions on Postfix logging see the Section 1.7, “Troubleshooting” [p. 239] section.
• Amavisd-new uses Syslog to send messages to /var/log/mail.log. The amount of detail can be increased by adding the $log_level option to /etc/amavis/conf.d/50-user, and setting the value
from 1 to 5.
$log_level = 2;
Note:
When the Amavisd-new log output is increased Spamassassin log output is also increased.
• The ClamAV log level can be increased by editing /etc/clamav/clamd.conf and setting the
following option:
LogVerbose true
By default ClamAV will send log messages to /var/log/clamav/clamav.log.
Note:
After changing an applications log settings remember to restart the service for the new settings to take affect. Also, once the issue you are troubleshooting is resolved it is a good idea to change the log settings back to normal.
See you in the next lesson
Mr.Mohamed samir™
Mailman for Ubuntu
Quoting one of e-books
4.Mailman
Mailman is an open source program for managing electronic mail discussions and e-newsletter lists.
Many open source mailing lists (including all the Ubuntu mailing lists17) use Mailman as their mailing list software. It is powerful and easy to install and maintain.
4.1. Installation
Mailman provides a web interface for the administrators and users, using an external mail server to send and receive emails. It works perfectly with the following mail servers:
• Postfix
• Exim
• Sendmail
• Qmail
We will see how to install and configure Mailman with, the Apache web server, and either the Postfix or Exim mail server. If you wish to install Mailman with a different mail server, please refer to the
references section.
Note:
You only need to install one mail server and Postfix is the default Ubuntu Mail Transfer
Agent.
Once exim4 is installed, the configuration files are stored in the /etc/exim4 directory. In Ubuntu, by default, the exim4 configuration files are split across different files. You can change this behavior by changing the following variable in the /etc/exim4/update-exim4.conf file:
dc_use_split_config='true'
Mailman:
To install Mailman, run following command at a terminal prompt:
sudo apt-get install mailman
It copies the installation files in /var/lib/mailman directory. It installs the CGI scripts in /usr/lib/cgibin/ mailman directory. It creates list linux user. It creates the list linux group. The mailman process will be owned by this user.
Configuration
This section assumes you have successfully installed mailman, apache2, and postfix or exim4. Now you just need to configure them.
Apache2
An example Apache configuration file comes with Mailman and is placed in /etc/mailman/ apache.conf. In order for Apache to use the config file it needs to be copied to /etc/apache2/ sites-available:
sudo cp /etc/mailman/apache.conf /etc/apache2/sites-available/mailman.conf
This will setup a new Apache VirtualHost for the Mailman administration site. Now enable the new configuration and restart Apache:
sudo a2ensite mailman.conf
sudo service apache2 restart
Mailman uses apache2 to render its CGI scripts. The mailman CGI scripts are installed in the /usr/lib/ cgi-bin/mailman directory. So, the mailman url will be http://hostname/cgi-bin/mailman/. You can
make changes to the /etc/apache2/sites-available/mailman.conf file if you wish to change this behavior.
Postfix
For Postfix integration, we will associate the domain lists.example.com with the mailing lists. Please replace lists.example.com with the domain of your choosing.
You can use the postconf command to add the necessary configuration to /etc/postfix/main.cf:
sudo postconf -e 'relay_domains = lists.example.com'
sudo postconf -e 'transport_maps = hash:/etc/postfix/transport'
sudo postconf -e 'mailman_destination_recipient_limit = 1'
In /etc/postfix/master.cf double check that you have the following transport:
mailman unix
- n n - - pipe
flags=FR user=list argv=/usr/lib/mailman/bin/postfix-to- ailman.py
${nexthop} ${user}
It calls the postfix-to-mailman.py script when a mail is delivered to a list.
Associate the domain lists.example.com to the Mailman transport with the transport map. Edit the file
/etc/postfix/transport:
lists.example.com mailman:
Now have Postfix build the transport map by entering the following from a terminal prompt:
sudo postmap -v /etc/postfix/transport
Then restart Postfix to enable the new configurations:
sudo /etc/init.d/postfix restart
Exim4
Once Exim4 is installed, you can start the Exim server using the following command from a terminal prompt:
sudo /etc/init.d/exim4 start
In order to make mailman work with Exim4, you need to configure Exim4. As mentioned earlier, by default, Exim4 uses multiple configuration files of different types. For details, please refer to
the Exim18 web site. To run mailman, we should add new a configuration file to the following configuration types:
• Main
• Transport
• Router
Exim creates a master configuration file by sorting all these mini configuration files. So, the order of these configuration files is very important.
Main
All the configuration files belonging to the main type are stored in the /etc/exim4/conf.d/main/ directory. You can add the following content to a new file, named 04_exim4-config_mailman:
# start
# Home dir for your Mailman installation -- aka Mailman's prefix
# directory.
# On Ubuntu this should be "/var/lib/mailman"
# This is normally the same as ~mailman
MM_HOME=/var/lib/mailman
#
# User and group for Mailman, should match your --with-mail-gid
# switch to Mailman's configure script. Value is normally "mailman"
MM_UID=list
MM_GID=list
#
# Domains that your lists are in - colon separated list
# you may wish to add these into local_domains as well
domainlist mm_domains=hostname.com
#
# -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
#
# These values are derived from the ones above and should not need
# editing unless you have munged your mailman installation
#
# The path of the Mailman mail wrapper script
MM_WRAP=MM_HOME/mail/mailman
#
# The path of the list config file (used as a required file when
# verifying list addresses)
MM_LISTCHK=MM_HOME/lists/${lc::$local_part}/config.pck
# end
Transport
All the configuration files belonging to transport type are stored in the /etc/exim4/conf.d/
transport/ directory. You can add the following content to a new file named 40_exim4-
config_mailman:
mailman_transport:
driver = pipe
command = MM_WRAP \
'${if def:local_part_suffix \
{${sg{$local_part_suffix}{-(\\w+)(\\+.*)?}{\$1}}} \
{post}}' \
$local_part
current_directory = MM_HOME
home_directory = MM_HOME
user = MM_UID
group = MM_GID
Router
All the configuration files belonging to router type are stored in the /etc/exim4/conf.d/router/
directory. You can add the following content in to a new file named 101_exim4-config_mailman:
mailman_router:
driver = accept
require_files = MM_HOME/lists/$local_part/config.pck
local_part_suffix_optional
local_part_suffix = -bounces : -bounces+* : \
-confirm+* : -join : -leave : \
-owner : -request : -admin
transport = mailman_transport
Stop:
The order of main and transport configuration files can be in any order. But, the order of router configuration files must be the same. This particular file must appear before the 200_exim4-config_primary file. These two configuration files contain same ype
of information. The first file takes the precedence. For more details, please refer to the references section.
Mailman
Once mailman is installed, you can run it using the following command:
sudo /etc/init.d/mailman start
Once mailman is installed, you should create the default mailing list. Run the following command to
create the mailing list:
sudo /usr/sbin/newlist mailman
Enter the email address of the person running the list: bhuvan at ubuntu.com
Initial mailman password:
To finish creating your mailing list, you must edit your /etc/aliases (or equivalent) file by adding the following lines, and possibly running the `newaliases' program:
## mailman mailing list
mailman: "|/var/lib/mailman/mail/mailman post mailman"
mailman-admin: "|/var/lib/mailman/mail/mailman admin mailman"
mailman-bounces: "|/var/lib/mailman/mail/mailman bounces mailman"
mailman-confirm: "|/var/lib/mailman/mail/mailman confirm mailman"
mailman-join: "|/var/lib/mailman/mail/mailman join mailman"
mailman-leave: "|/var/lib/mailman/mail/mailman leave mailman"
mailman-owner: "|/var/lib/mailman/mail/mailman owner mailman"
mailman-request: "|/var/lib/mailman/mail/mailman request mailman"
mailman-subscribe: "|/var/lib/mailman/mail/mailman subscribe mailman"
mailman-unsubscribe: "|/var/lib/mailman/mail/mailman unsubscribe mailman"
Hit enter to notify mailman owner...
#
We have configured either Postfix or Exim4 to recognize all emails from mailman. So, it is not mandatory to make any new entries in /etc/aliases. If you have made any changes to the configuration files, please ensure that you restart those services before continuing to next section.
Note:
The Exim4 does not use the above aliases to forward mails to Mailman, as it uses a discover approach. To suppress the aliases while creating the list, you can add MTA=None line in Mailman configuration file, /etc/mailman/mm_cfg.py.
Administration
We assume you have a default installation. The mailman cgi scripts are still in the /usr/lib/cgi-bin/
mailman/ directory. Mailman provides a web based administration facility. To access this page, point your browser to the following url:
http://hostname/cgi-bin/mailman/admin
The default mailing list, mailman, will appear in this screen. If you click the mailing list name, it will ask for your authentication password. If you enter the correct password, you will be able to change administrative settings of this mailing list. You can create a new mailing list using the command line utility (/usr/sbin/newlist). Alternatively, you can create a new mailing list using the web interface.
Users:
Mailman provides a web based interface for users. To access this page, point your browser to the following url:
http://hostname/cgi-bin/mailman/listinfo
The default mailing list, mailman, will appear in this screen. If you click the mailing list name, it will display the subscription form. You can enter your email address, name (optional), and password to
subscribe. An email invitation will be sent to you. You can follow the instructions in the email to subscribe.
See you in the next lesson
Mr.Mohamed samir™